So You Want to Onboard a Compliance Tool
You've demoed three platforms. Watched the onboarding videos. Compared pricing spreadsheets. The team's excited. You sign the contract, kick off implementation, and wait for compliance to become... handled.
But six months later, you're still emailing CSVs to your carrier. Your ops person is running the same spreadsheet on the side "because the system doesn't track everything." And that beautiful dashboard you saw in the demo? Nobody's logged into it since February.
Here's what nobody tells you during the sales process: compliance tools rarely fix process debt by themselves; they usually expose it. Therefore, the real work starts after you buy the tool, not before.
The six steps every COO misses
Most MGAs approach compliance software like they're buying a solution. But you're not buying a solution—you're buying infrastructure. And infrastructure only works if you build on top of it correctly.
Step 1: Start with the lifecycle, not the logo.
Before you touch a platform, map your producer journey. Not the software's workflow—your workflow.
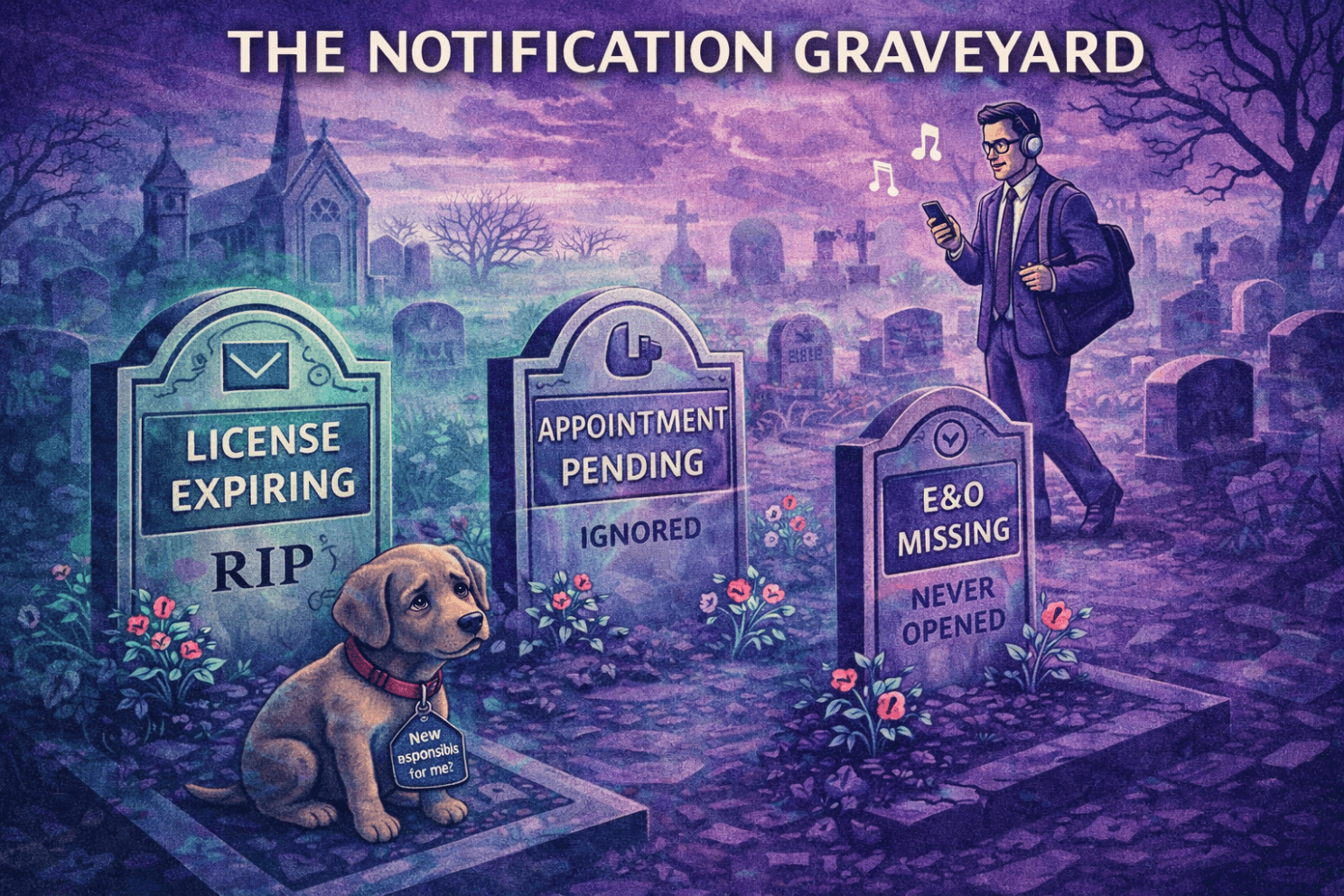
In most MGAs, producers move through four practical stages: onboarding, active selling, monitoring and renewal, and termination. But most MGAs buy a tool before defining who owns each stage—and therefore alerts go unread, tasks go unassigned, and the system becomes a notification graveyard.
Draw it on a whiteboard. Who touches the producer at each stage? What triggers the transition? What documentation is required? If you can't answer these questions without the software, the software won't answer them for you.
Step 2: Assign ownership, not hope.
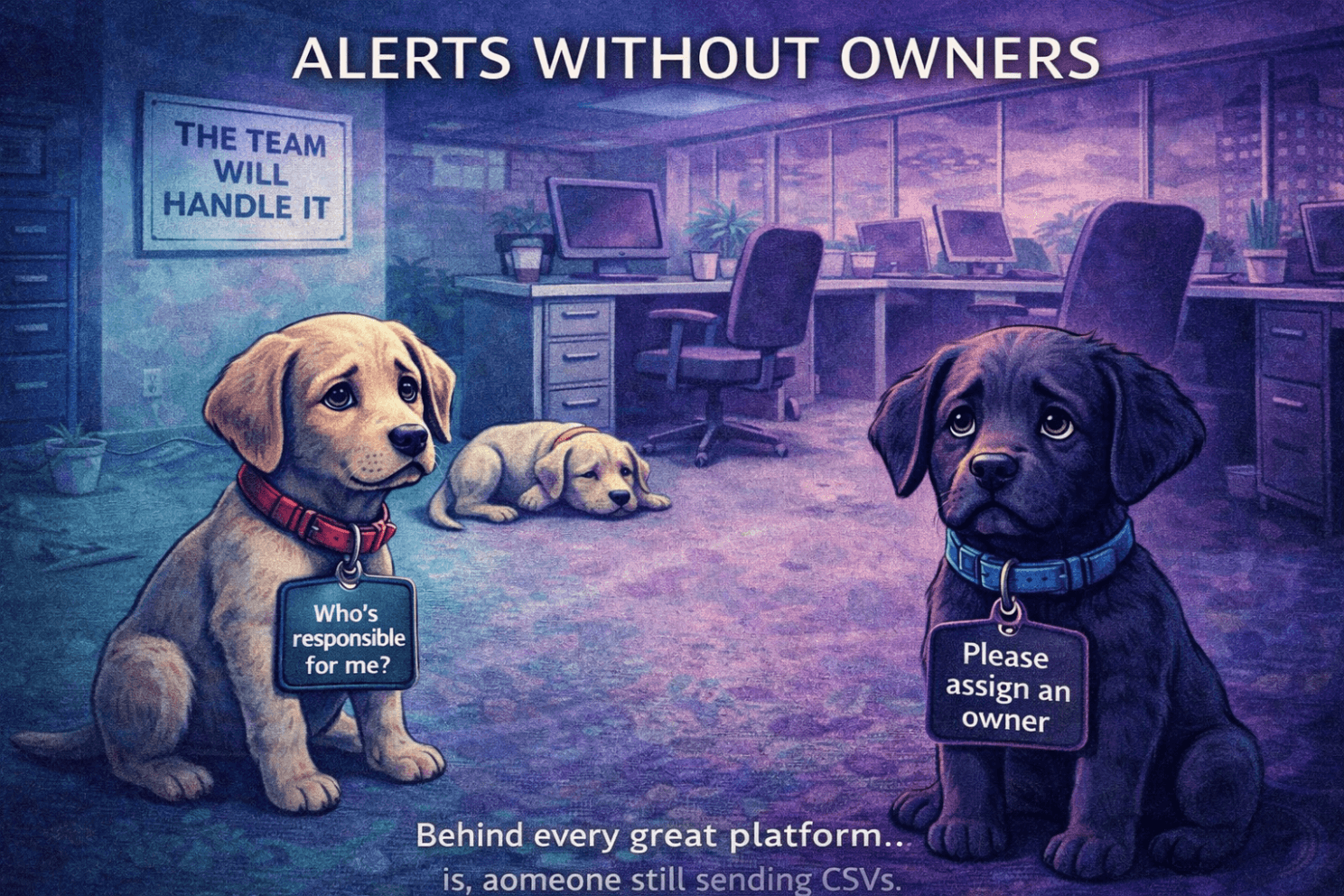
Compliance is a team sport. But "the team" isn't an owner—it's an excuse.
For every control point in your compliance process, you need a name. Who monitors license expirations? Who manages carrier appointments? Who validates that terminations are actually completed? Who responds when an alert fires?
If the answer to any of these is "someone on the ops team" or "we all keep an eye on it," you've got a gap. Therefore, when something slips, nobody's accountable—and nothing changes.
Write down names. Assign backup owners. Make it explicit. A compliance tool can send alerts all day, but alerts without owners are just noise.
Step 3: Translate rules into workflows.
Here's where most implementations fall apart: the tool can automate reminders, but only if you define what action follows each one.
Think of your compliance requirements like code. Every rule should have a trigger and a response:
License expires in 30 days → alert Compliance Lead → suspend bind access if unrenewed at 7 days.
E&O certificate missing → flag producer file → block new appointments until resolved.
Appointment pending 30+ days → escalate to ops manager → manual carrier follow-up.
But most MGAs set up the alerts and assume action will follow. Therefore, the system generates notifications that pile up in someone's inbox until they start ignoring them entirely. Alerts without consequences aren't controls—they're suggestions.
Step 4: Connect the dots.
Your compliance tool doesn't exist in isolation. It needs to talk to your PAS, your CRM, and probably your carrier portals.
Here's how to think about it: Your PAS owns policy data. Your CRM owns producer relationships. Your compliance platform owns proof and eligibility. But none of them tell the full story alone—your audit trail depends on their integration.
Therefore, if these systems don't sync, you end up with three different versions of "truth" and no way to reconcile them quickly. The auditor asks a simple question, and you're spending three days pulling data from multiple sources and hoping the dates align.
Build integration discipline early. Set a regular sync cadence (nightly is common if integrations allow it). Maintain an audit trail of key changes (status, license/appointment, access) Log every data change. Pick one system of record per entity type and make everything else defer to it.
This is where expensive legacy platforms often disappoint. They promise "enterprise integration" can turn into long implementations that under-deliver if integration scope isn’t nailed down i.e. six months of your team showing up to weekly calls to ‘check in’. Therefore, you end up paying premium prices for a tool that still requires manual reconciliation—which defeats the entire purpose.
Step 5: Calibrate alerts and exceptions.
Automation without thresholds equals noise. And noise creates compliance fatigue—the state where your team starts ignoring alerts because there are too many to process.
Create severity tiers:
Green: License expiring in 45+ days → automated reminder to producer.
Yellow: Appointment pending 30+ days → escalate to ops manager.
Red: Unlicensed binding attempt → immediate system lockout.
Not everything is urgent. But if everything looks urgent, nothing gets prioritized. Therefore, your most critical alerts get buried in a sea of routine notifications, and the thing that actually matters gets missed.
Spend time tuning your alert thresholds after implementation. What seemed right in theory often needs adjustment once you see real data flowing through the system.
Step 6: Audit your own implementation.
Here's the step everyone skips: treating your compliance setup like a living system that needs maintenance.
Quarterly, consider spot-checking five random producers. Pull their full compliance file—licenses, appointments, E&O, authority levels. Does the system match reality? Are there gaps the automation missed?
Annually, verify that your system rules still align with carrier requirements. Binders change. Authority limits get updated. State requirements evolve. But system configurations often don't—therefore your automation slowly drifts out of sync with your actual obligations.
Audits aren't just for regulators. They're how you prove your own system still works before someone else tests it for you.
The common failure modes
"We bought the Ferrari but never filled the gas tank." The tool is powerful, but the data discipline isn't there. Garbage in, garbage out—except now you've paid mid five figures for the privilege of automating your garbage.
"Everything's in the system, except the latest E&O." Document governance falls apart because nobody owns the update process. The system shows green, but the actual certificate expired three months ago. Therefore, you have false confidence, which is worse than no confidence.
"We assumed alerts meant action." The notifications are firing. The dashboards look busy. But nobody's actually responding, and the tool has become an elaborate way to document problems you're not fixing.
Each failure has the same root cause: thinking a compliance tool replaces compliance thinking. But tools don't create accountability—they just make good processes run faster. If your process is broken, automation just breaks it faster.
What it looks like when it works
When implementation is done right, the payoff is real:
Near real-time visibility and far fewer manual NIPR checks. Faster onboarding because the workflow is defined and the handoffs are automatic. Carriers trust your data because you can produce documentation in minutes, not days.
But more importantly: you can prove that every producer and policy are in sync—from appointment to audit—without heroic effort. The system does what it's supposed to do, and your team focuses on exceptions rather than routine verification.
That's not magic. That's good architecture.
A well-implemented modern platform (like ProducerFlow) will absolutely make your life easier—but only when it’s built on clear ownership, enforced workflows, and disciplined data hygiene.
Compliance is a muscle, not a module
Here's the truth nobody wants to hear during a software evaluation: the best MGAs don't have the best tools—they have the best habits.
A well-implemented modern platform will absolutely make your life easier. It will automate the tedious stuff, surface problems early, and give you audit-ready documentation on demand. But it won't build the muscle for you.
Start small. One alert workflow, fully owned and consistently actioned. One checklist that actually gets completed. One audit rhythm that happens quarterly whether you feel like it or not.
The tool is leverage. But leverage only works if you're already pushing in the right direction.
So yes—buy the tool. But more importantly, build the muscle. Because that's what earns you carrier capacity, clean audits, and the operational credibility that lets you scale without chaos.
Details vary by state, carrier, and delegation model—so treat these as control patterns, not universal requirements.
One clarification that matters in practice: state compliance and carrier compliance are related but not interchangeable. State regulators care about licensing, CE, and consumer protection. Carriers care about authority, appointments, underwriting controls, and whether you followed their rules.
Your architecture has to satisfy both—often with different evidence, different timelines, and different reviewers. If your system treats “compliant” as a single green checkmark, you’re oversimplifying a problem that auditors won’t
Your turn
If you've already implemented a compliance platform, when was the last time you audited whether the system rules still match your actual carrier requirements? If you haven't checked in the last six months, that's your weekend homework.
Authors: Michelle Bothe & Ido Deutsch
About Producerflow
Producerflow is a modern platform designed to simplify producer management for insurance carriers, MGAs, and large agencies. By centralizing onboarding, compliance, licensing, and data integrations, Producerflow helps teams reduce operational friction, mitigate regulatory risk, and scale distribution with confidence.
Published
February 9, 2026